基于OSSIM平臺(tái)的漏洞掃描詳解
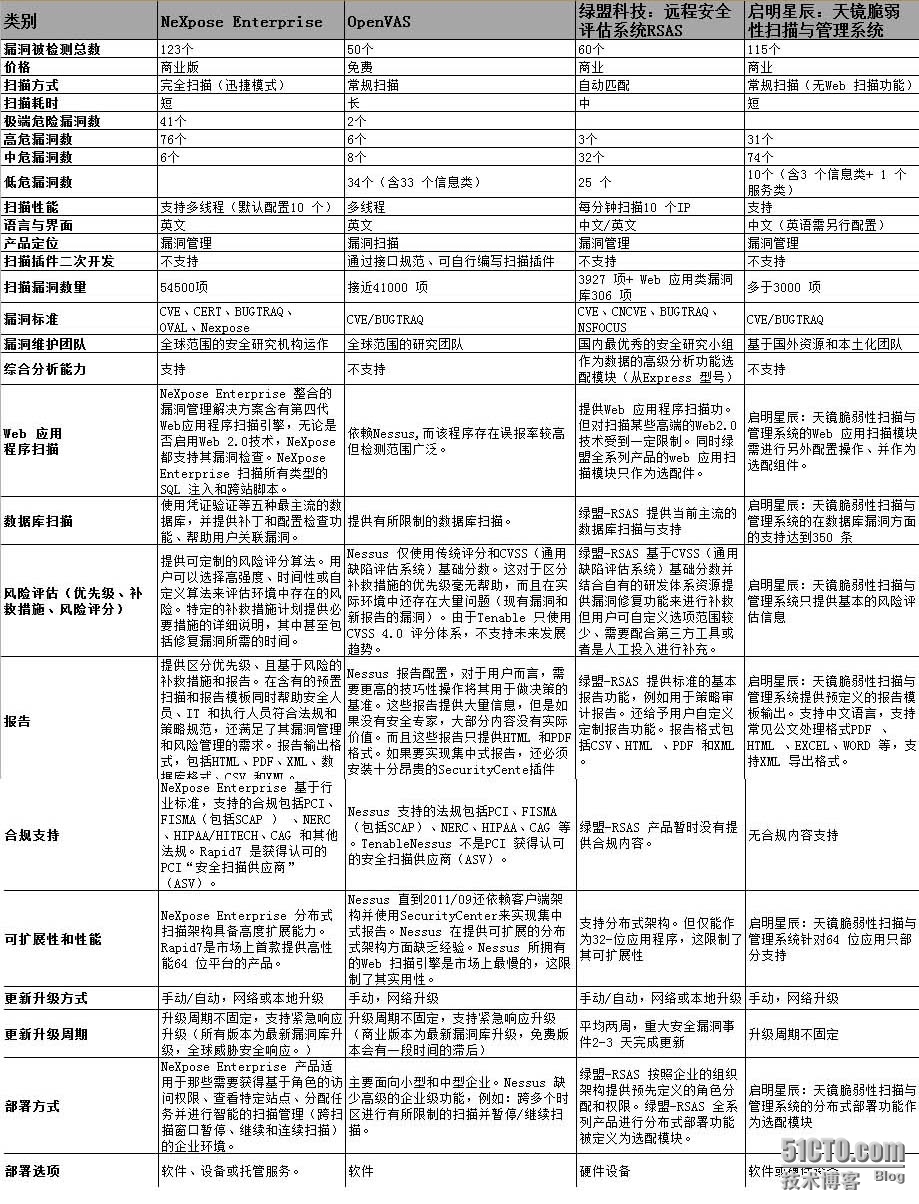
Openvas是一套開(kāi)源漏洞掃描系統(tǒng),如果手動(dòng)搭建需要復(fù)雜的過(guò)程,花費(fèi)不少人力和時(shí)間成本,因?yàn)樗翘酌赓M(fèi)的漏洞掃描系統(tǒng),功能上不遜色于商業(yè)版的漏洞掃描器,受到不少用戶的青睞,下表對(duì)比了NeXpose、RSAS和啟明的漏洞掃描器的主要功能。
有了以上背景之后,下文主要針對(duì)OSSIM平臺(tái)下如何以圖形化方式操作漏洞掃描的過(guò)程。
準(zhǔn)備工作:首先確保沒(méi)有運(yùn)行的掃描進(jìn)程和任務(wù)
掃描漏洞同時(shí)升級(jí)漏洞庫(kù)會(huì)導(dǎo)致升級(jí)失敗。
第一步:同步插件
- #openvas-nvt-sync
- [i] This script synchronizes an NVT collection with the 'OpenVAS NVT Feed'.
- [i] The 'OpenVAS NVT Feed' is provided by 'The OpenVAS Project'.
- [i] Online information about this feed: 'http://www.openvas.org/openvas-nvt-feed.html'.
- [i] NVT dir: /var/lib/openvas/plugins
- [i] Will use rsync
- [i] Using rsync: /usr/bin/rsync
- [i] Configured NVT rsync feed: rsync://feed.openvas.org:/nvt-feed
- OpenVAS feed server - http://www.openvas.org/
- This service is hosted by Intevation GmbH - http://intevation.de/
- All transactions are logged.
- Please report synchronization problems to openvas-feed@intevation.de.
- If you have any other questions, please use the OpenVAS mailing lists
- or the OpenVAS IRC chat. See http://www.openvas.org/ for details.
- receiving incremental file list
- deleting gb_openssl_38562.nasl.asc
- deleting gb_openssl_38562.nasl
- ./
- COPYING
- 588 100% 574.22kB/s 0:00:00 (xfer#1, to-check=13347/13355)
- COPYING.GPLv2
- 18002 100% 17.17MB/s 0:00:00 (xfer#2, to-check=13346/13355)
- COPYING.files
- 1819904 100% 1.77MB/s 0:00:00 (xfer#3, to-check=13345/13355)
- DDI_Directory_Scanner.nasl
- 32957 100% 32.74kB/s 0:00:00 (xfer#4, to-check=13342/13355)
- DDI_Directory_Scanner.nasl.asc
- 198 100% 0.20kB/s 0:00:00 (xfer#5, to-check=13341/13355)
- ... ...
同步數(shù)萬(wàn)個(gè)插件時(shí)間比較長(zhǎng),消耗資源不大,可以去喝杯咖啡啦,或者了解一下插件的組成。
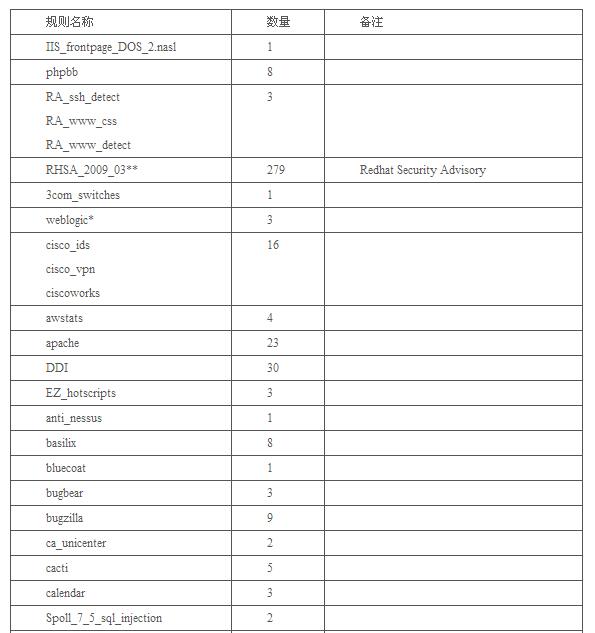
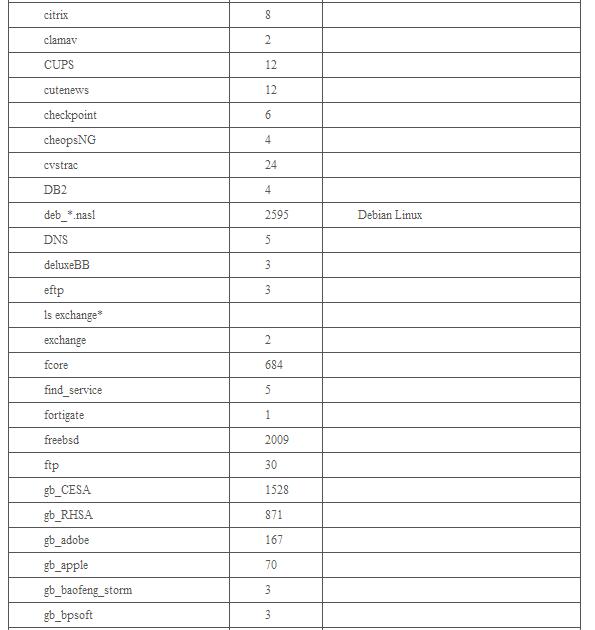
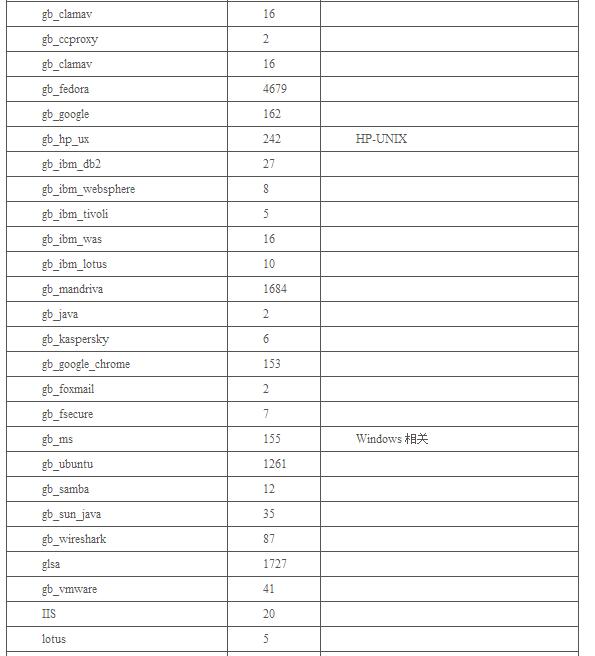
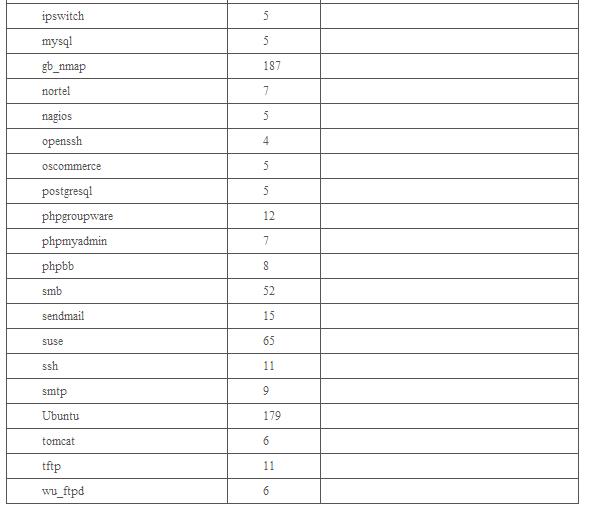
表1 Openvas主要腳本分類(lèi)及分布情況
第二步:更新插件(做這一步操作,建議在輕負(fù)載下進(jìn)行)
#perl /usr/share/ossim/scripts/vulnmeter/updateplugins.pl migrate /* 比較消耗CPU和磁盤(pán)I/O */
2015-09-07 07:27:33 Framework profile has been found...
2015-09-07 07:27:33 Deleting all tasks in 192.168.11.150 ...
2015-09-07 07:27:33 updateplugins: configured to not updateplugins
2015-09-07 07:27:33 updateplugins: configured to not repair DB
2015-09-07 07:27:33 BEGIN - DUMP PLUGINS
2015-09-07 07:29:01 FINISH - DUMP PLUGINS [ Process took 88 seconds ]
2015-09-07 07:29:01 BEGIN - IMPORT PLUGINS
2015-09-07 07:30:00 FINISH - IMPORT PLUGINS [ 40473 plugins - Process took 59 seconds ]
2015-09-07 07:30:00 BEGIN - UPDATE CATEGORIES
2015-09-07 07:30:00 FINISH - UPDATE CATEGORIES [ Process took 0 seconds ]
2015-09-07 07:30:00 BEGIN - UPDATE FAMILIES
2015-09-07 07:30:00 FINISH - UPDATE FAMILIES [ Process took 0 seconds ]
2015-09-07 07:30:00 BEGIN - UPDATE OPENVAS_PLUGINS
2015-09-07 07:30:03 FINISH - UPDATE OPENVAS_PLUGINS [ Process took 3 seconds ]
2015-09-07 07:30:03 BEGIN - UPDATE NESSUS_PREFERENCES
2015-09-07 07:30:03 show tables like "vuln_nessus_preferences_defaults"
2015-09-07 07:30:03 updateprefs: Getting plugin preferences
2015-09-07 07:30:05 FINISH - UPDATE NESSUS_PREFERENCES [ Process took 2 seconds ]
2015-09-07 07:30:06 Creating Deep profile...
2015-09-07 07:30:06 Filling categories...............
2015-09-07 07:30:06 Done
2015-09-07 07:30:06 Filling families.............................................................
2015-09-07 07:30:06 Done
2015-09-07 07:30:06 Filling plugins...
2015-09-07 07:30:13 Filling preferences in Alienvault DB...
2015-09-07 07:30:14 Done
2015-09-07 07:30:14 Deep profile inserted
2015-09-07 07:30:15 Creating Default profile...
2015-09-07 07:30:15 Filling categories...............
2015-09-07 07:30:15 Done
2015-09-07 07:30:15 Filling families.............................................................
2015-09-07 07:30:15 Done
2015-09-07 07:30:15 Filling plugins...
2015-09-07 07:30:23 Filling preferences in Alienvault DB...
2015-09-07 07:30:24 Done
2015-09-07 07:30:24 Default profile inserted
2015-09-07 07:30:24 Creating Ultimate profile...
2015-09-07 07:30:24 Filling categories...............
2015-09-07 07:30:24 Done
2015-09-07 07:30:24 Filling families.............................................................
2015-09-07 07:30:24 Done
2015-09-07 07:30:24 Filling plugins...
2015-09-07 07:30:32 Filling preferences in Alienvault DB...
2015-09-07 07:30:33 Done
2015-09-07 07:30:33 Ultimate profile inserted
2015-09-07 07:30:33 BEGIN - UPDATE PORT SCANNER
2015-09-07 07:30:35 FINISH - UPDATE PORT SCANNER [ Process took 2 seconds ]
Updating plugin_sid vulnerabilities scanner ids
plugins fetched
Updating...
Script id:94151, Name:IT-Grundschutz M4.288: Sichere Administration von VoIP-Endger?ten, Priority:0
Script id:703073, Name:Debian Security Advisory DSA 3073-1 (libgcrypt11 - security update), Priority:1
Script id:804624, Name:Adobe Reader Plugin Signature Bypass Vulnerability (Windows), Priority:2
Script id:868149, Name:Fedora Update for kernel FEDORA-2014-9959, Priority:5
Script id:95048, Name:IT-Grundschutz M5.145: Sicherer Einsatz von CUPS, Priority:0
Script id:842216, Name:Ubuntu Update for linux USN-2616-1, Priority:4
Script id:105036, Name:OpenVPN Detection, Priority:0
Script id:868005, Name:Fedora Update for audacious-plugins FEDORA-2014-8183, Priority:1
Script id:869350, Name:Fedora Update for springframework FEDORA-2015-6862, Priority:5
… …
Script id:105084, Name:Multiple ManageEngine Products Arbitrary File Upload Vulnerability, Priority:3
Script id:867751, Name:Fedora Update for python-keystoneclient FEDORA-2014-5555, Priority:3
Script id:882209, Name:CentOS Update for nss CESA-2015:1185 centos6, Priority:2
Script id:842209, Name:Ubuntu Update for libmodule-signature-perl USN-2607-1, Priority:5
經(jīng)過(guò)一刻鐘等待終于更新完成。注意,該過(guò)程需要一氣呵成,中途不能強(qiáng)制退出。
下面用時(shí)間軸表示每個(gè)步驟的演進(jìn)順序和所花費(fèi)的時(shí)間,如下圖所示。從某日的00:34:34開(kāi)始到00:38:50結(jié)束的過(guò)程。
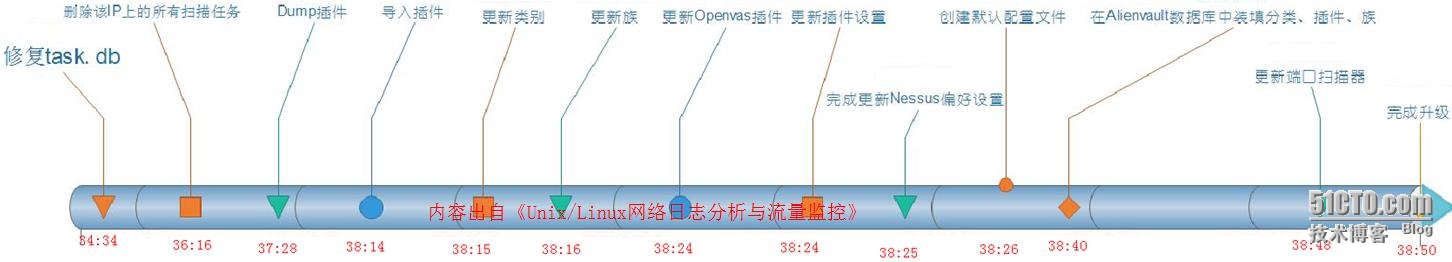
如果有些用戶不習(xí)慣在CLI下操作升級(jí)命令,這一工作同樣可以在WebUI中完成。
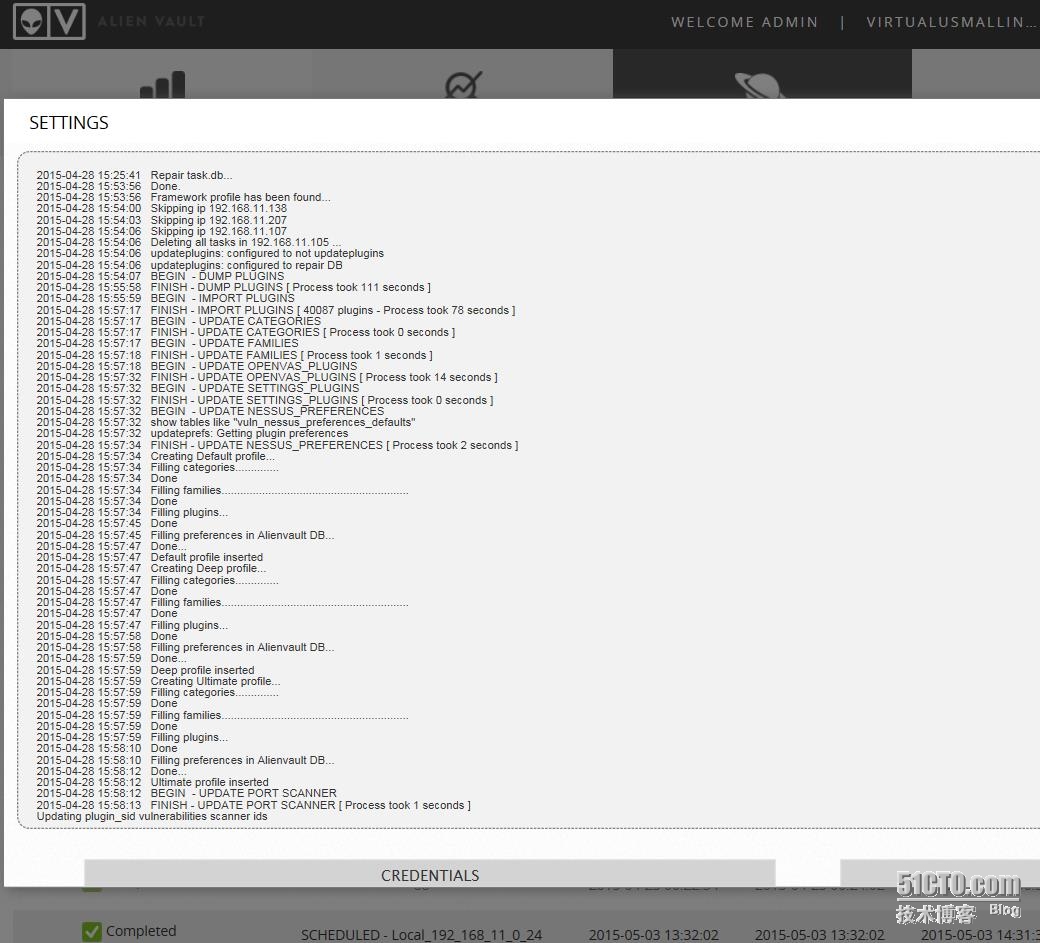
第三步:驗(yàn)證更新
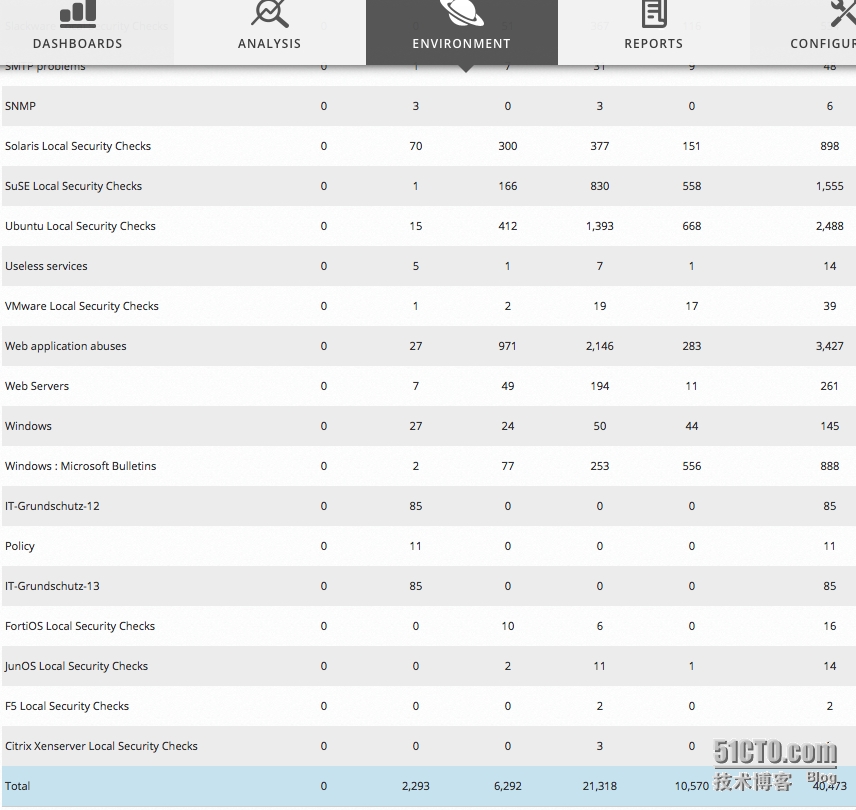
我們看到最后一行顯示總數(shù)為40473,這個(gè)數(shù)值和下載的插件數(shù)量一直,代表升級(jí)完成。
注意:漏洞升級(jí)視頻大家可訪問(wèn):http://www.tudou.com/programs/view/kyTmc42Ky14/
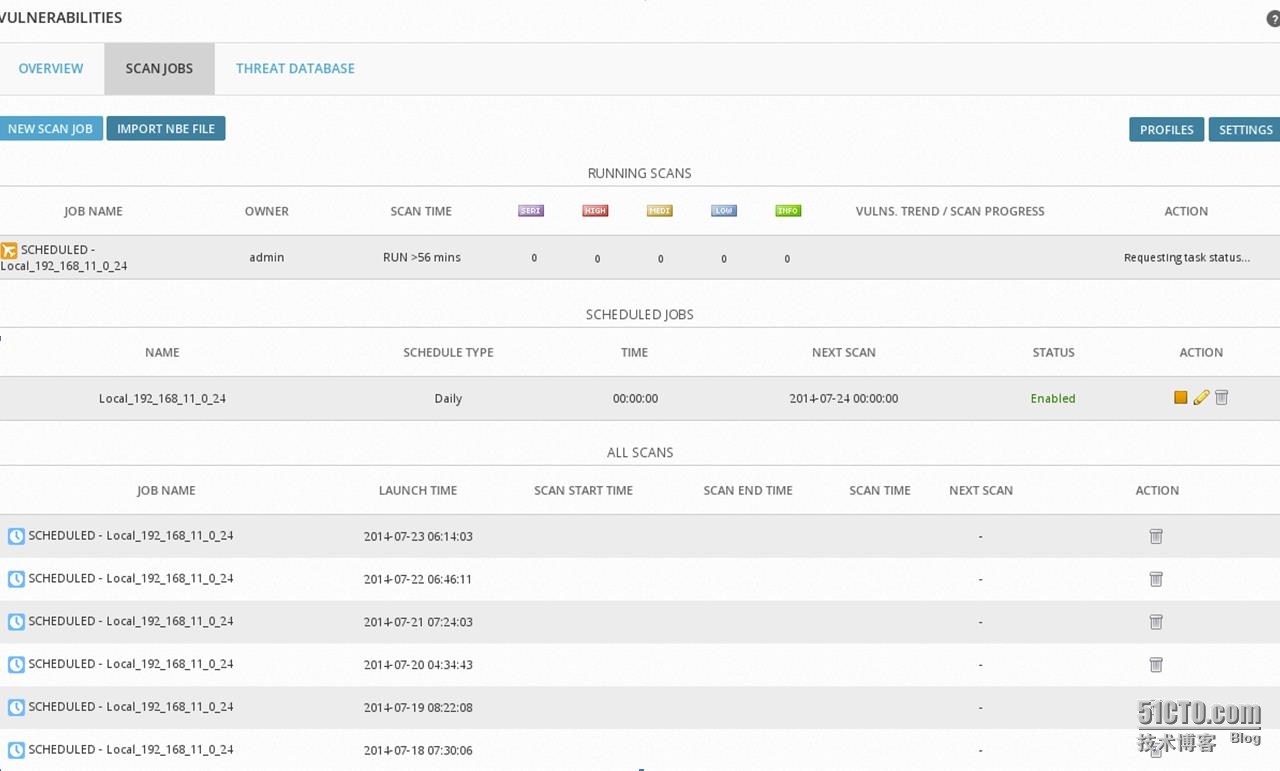
第四步:開(kāi)始漏洞掃描-定制策略
首先掃描資產(chǎn),建立資源池,這里就不詳細(xì)介紹。在OSSIM系統(tǒng)里默認(rèn)定義了三種策略,默認(rèn)為Default,該策略最為常用。
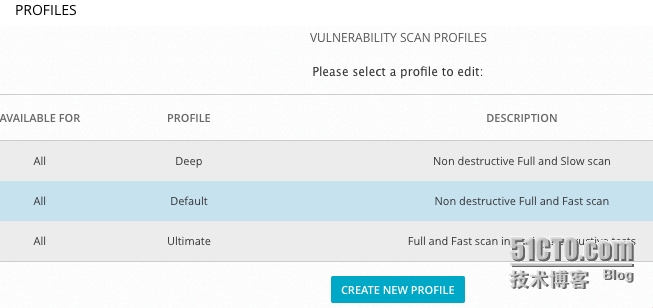
如果需要更改策略,請(qǐng)點(diǎn)擊CREATE NEW PROFILE按鈕。
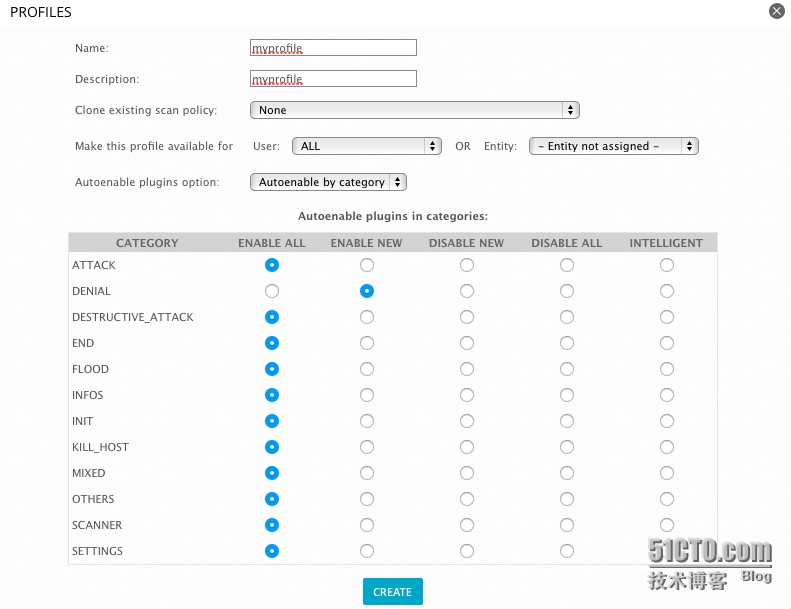
接著開(kāi)始掃描,填寫(xiě)任務(wù)名稱(chēng),選擇Sensor,選擇策略,選擇資源池內(nèi)的主機(jī),最后點(diǎn)擊新建任務(wù)按鈕。
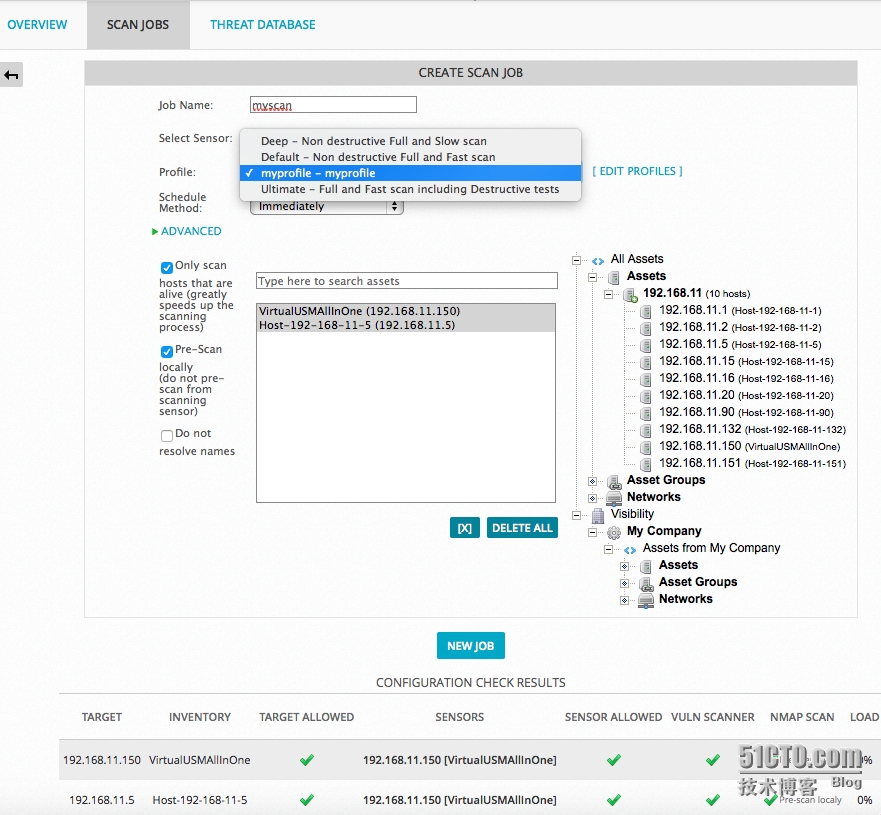
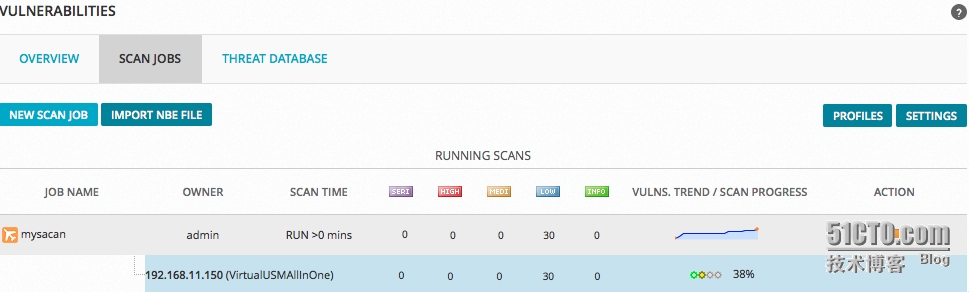
掃描準(zhǔn)備
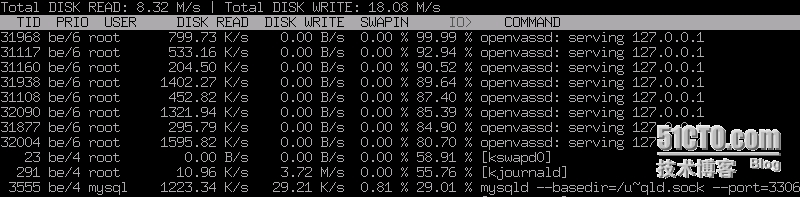
漏洞掃描時(shí)那些進(jìn)程最繁忙?
Htop是Linux系統(tǒng)中的一個(gè)互動(dòng)的進(jìn)程查看工具,該命令可以幫助管理員了解掃描發(fā)生的變化。#htop -d 50
一次掃描多少機(jī)器合適?
如果所監(jiān)控網(wǎng)段服務(wù)器數(shù)量超過(guò)25臺(tái),這里假設(shè)是100臺(tái),那么至少分4次掃描,例如直接輸入“192.168.11.0/24”,這樣表示一個(gè)網(wǎng)段,那么OSSIM系統(tǒng)負(fù)載將會(huì)明顯增大,掃描等待時(shí)間明顯延長(zhǎng),可能會(huì)長(zhǎng)達(dá)數(shù)天,直到超過(guò)一個(gè)計(jì)劃任務(wù)的周期,這樣可能造成一個(gè)惡性循環(huán),直到拖垮整個(gè)系統(tǒng)。
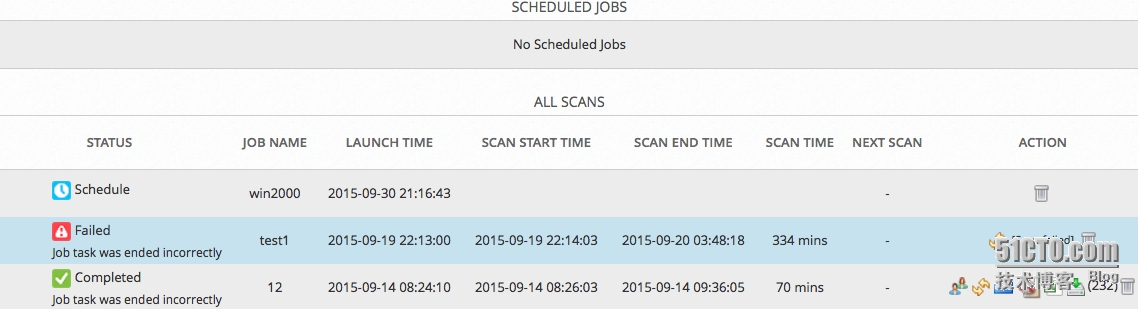
進(jìn)過(guò)300多分鐘都沒(méi)有結(jié)束的任務(wù)最后逃脫不了失敗的命運(yùn)。
掃描結(jié)果分析
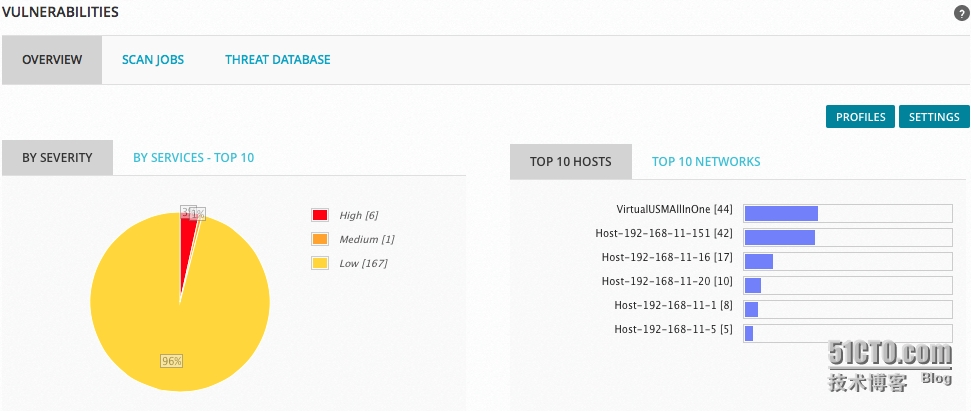
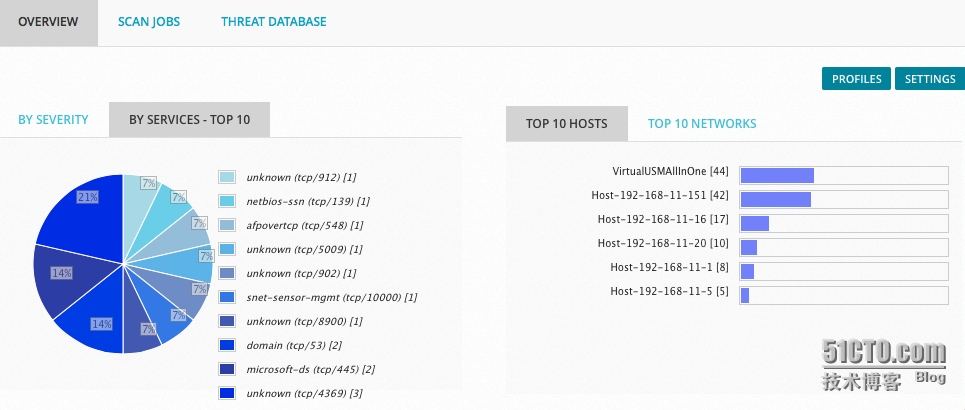
不過(guò)在分析時(shí),談到“過(guò)時(shí)”的漏洞問(wèn)題,在一些古老些操作系統(tǒng)Windows NT/2000、Solaris7/8、Linux(2.2 、2.4內(nèi)核)曾經(jīng)存在的那些系統(tǒng)漏洞、網(wǎng)絡(luò)服務(wù)器漏洞,在現(xiàn)代系統(tǒng)中已經(jīng)絕跡,受影響系統(tǒng)已經(jīng)被修復(fù),這種漏洞變得沒(méi)有任何價(jià)值。對(duì)這些系統(tǒng)進(jìn)行漏洞掃描變得沒(méi)有意義。